TL;DR: Tasked with modernizing an application with no source code? This guide is your playbook. Learn the two key phases of software reverse engineering—dynamic analysis (watching it run) and static analysis (inspecting the code)—and the modern tools that make it possible, all within an ethical framework.
You’ve been handed a mission. There’s a critical application, probably a compiled .exe or a set of .dll files, sitting on a server. It runs an essential part of the business. And you’ve been asked to integrate it with a new platform, or maybe even replace it.
There’s just one problem: there is no source code. No documentation. The original developers vanished a decade ago. It’s a black box.
This isn’t hacking. You’re not trying to break in. You’re trying to understand. This is software archaeology: the methodical, scientific process of unearthing the secrets of a legacy system to preserve its logic and safely bring it into the modern world. This guide is your set of excavation tools.
🤔 First, A Word on Ethics and Legality
Before we dig in, we need to set up the site properly. This is the most important section of this article.
The techniques described here are for analyzing software when you have a legitimate, legal right to do so. This typically means the software is an asset owned by your company. You are trying to understand your own property.
Attempting to decompile or reverse engineer software you do not own can violate its End-User License Agreement (EULA) and may be illegal. The goal is documentation and migration, not intellectual property theft.
Disclaimer: I’m not a lawyer. Before you begin any project involving reverse engineering, you must consult with your company’s legal department to ensure you are operating within legal and contractual boundaries.
🏛️ The Two Pillars of Software Archaeology
A good archaeological dig happens in phases. You don’t just start digging holes randomly. The same is true for reverse engineering. The entire process rests on two fundamental pillars of analysis.
- Dynamic Analysis (The Behavioral Study): This is the process of watching the application while it’s running. You don’t look at the code. Instead, you observe its behavior from the outside. What files does it touch? What servers does it talk to? What data does it send? It’s about understanding what the application does.
- Static Analysis (The Structural Study): This is the process of examining the application’s files while it is not running. You look inside the box. This is where you’ll use tools like decompilers and disassemblers to try and reconstruct the source code and understand what the application is.
Always start with dynamic analysis. It’s less invasive and provides crucial context that will make the static analysis phase much more productive.
🕵️♂️ Phase 1: Dynamic Analysis – The Observation Deck
In this phase, your goal is to map the application’s ecosystem. You are an observer, watching how the black box interacts with its environment.
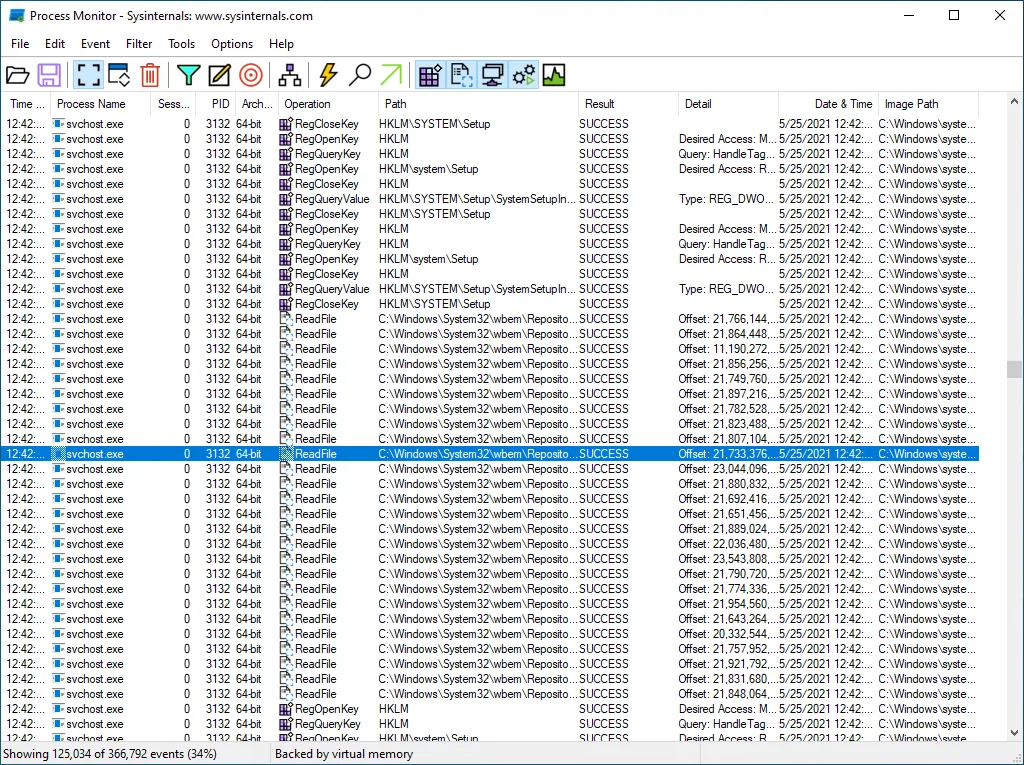
Tool 1: Process Monitoring with ProcMon
The undisputed king of this domain is Process Monitor (ProcMon), a free tool from Microsoft’s Sysinternals suite. It shows you every file access, registry read/write, and process/thread activity in real-time.
How to use it:
- Start ProcMon.
- Set up a filter to only show events from your target application’s
.exefile. - Start your application and use its features.
- Look for clues:
- File Access: Is it reading a
.inior.xmlfile on startup? That’s likely its configuration file. Is it writing to a log file? - Registry Access: Is it reading settings from
HKEY_LOCAL_MACHINE? This tells you how it’s configured. - Process Activity: Is it launching other executables?
- File Access: Is it reading a
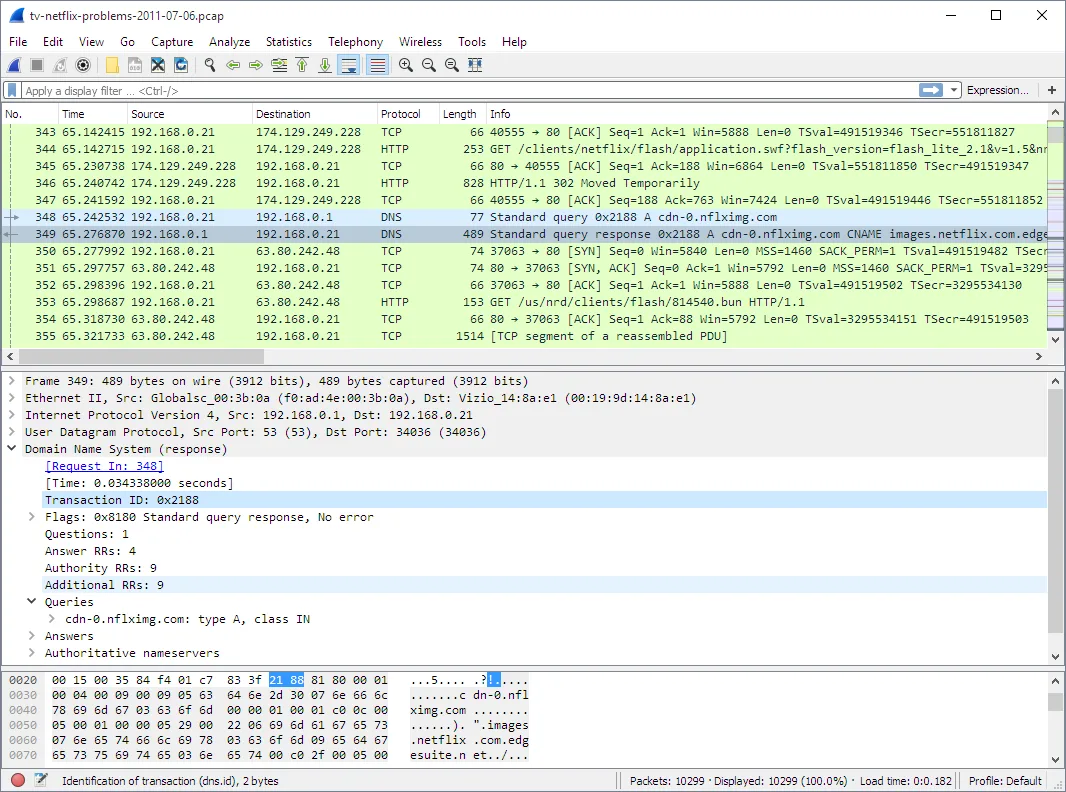
Tool 2: Network Traffic Analysis with Wireshark
If your application communicates over a network, you need to know what it’s saying. Wireshark is the industry-standard tool for this. It captures every single packet going in and out of your network card.
How to use it:
- Start Wireshark and select the correct network interface.
- Use the application.
- Stop the capture and filter by the IP address of the server your application is talking to.
- Analyze the conversation: Is it connecting to a database? You’ll see traffic on ports like 1433 (SQL Server) or 5432 (PostgreSQL). Is it calling a web service? You’ll see HTTP traffic.
Tool 3: HTTP(S) Monitoring with Fiddler
For applications that specifically talk to web services, Wireshark can be overkill. Fiddler is a much more user-friendly tool that acts as a proxy, neatly showing you all HTTP and HTTPS requests and responses in a clean interface.
Insight: At the end of the dynamic analysis phase, you should be able to draw a diagram. This diagram shows the black box in the center, with arrows pointing to the configuration files it reads, the log files it writes, the databases it connects to, and the APIs it calls. You have mapped its entire world without once looking at its code.
🔬 Phase 2: Static Analysis – Inside the Code
Now that you know how the application behaves, it’s time to open it up and see how it’s built. This is where you’ll look at the compiled code itself.
Understanding the Layers: Disassemblers vs. Decompilers
These terms sound similar, but they are critically different.
| Tool Type | What it Does | Resulting Output | Best For… |
|---|---|---|---|
| Disassembler | Converts binary machine code into human-readable Assembly language (ASM). | Low-level & hard to read. A direct translation of the machine’s instructions. | Native applications (C, C++, Delphi) where direct decompilation is impossible. |
| Decompiler | Attempts to reverse the compilation process, recreating high-level source code. | High-level & much easier to read. Looks similar to the original C#, Java, etc. | Managed code applications (.NET, Java) and some native code. |
You will always prefer a decompiler if one is available and effective for your application’s language.
The Modern Archaeologist’s Toolkit
- For .NET (C#, VB.NET): You’re in luck. .NET applications contain metadata that makes decompilation highly effective.
- JetBrains dotPeek: A free, excellent decompiler that can open almost any
.exeor.dlland show you the C# code. - ILSpy: Another fantastic open-source alternative.
- JetBrains dotPeek: A free, excellent decompiler that can open almost any
- For Java: Similar to .NET, Java bytecode is reversible.
- JD-GUI: A simple drag-and-drop tool that decompiles
.jarfiles back to Java source code.
- JD-GUI: A simple drag-and-drop tool that decompiles
- For Native Code (C, C++, Delphi, COBOL): This is the hard mode of software archaeology. Decompilation is often imperfect or impossible. Here, you’ll rely on powerful disassemblers.
- Ghidra: Developed and open-sourced by the U.S. National Security Agency (NSA). It’s an incredibly powerful and free framework for deep analysis of binary files.
- IDA Pro: The commercial industry standard for decades. Extremely powerful, but also very expensive.
This level of deep static analysis is often a necessity in the most challenging legacy environments. For example, it’s a core activity in the modernization of COBOL mainframe applications, where the business logic is decades old and completely opaque.
📜 The Final Step: Document Everything
The ultimate goal of archaeology is to create a map of the ancient city you’ve unearthed. Your reverse engineering project is no different. The final deliverable is not just “understanding,” but a concrete documentation package that your team can use to move forward.
This package should include:
- An architectural diagram showing all the components and their interactions (based on your dynamic analysis).
- A list of all external dependencies (files, registry keys, databases, APIs).
- Flowcharts or pseudocode documenting the critical business logic you uncovered from the decompiled code.
- A data dictionary for any databases it uses.
This documentation is the priceless artifact you’ve recovered. It turns the dangerous black box into a known quantity. This effort is often the critical first step in any successful migration, forming the foundation of the strategy detailed in our Legacy System Modernization Guide.
❓ FAQ: Reverse Engineering Questions
Is this process guaranteed to work?
No. Success depends on the language the application was written in, the complexity of its logic, and whether the original developers used any anti-reverse engineering techniques. .NET and Java are generally the easiest to analyze; old C++ or Delphi applications are much harder.
What about applications with anti-tamper or obfuscation?
Code obfuscation is a technique used to make decompiled code intentionally hard to read. Anti-tamper and anti-debugging tools are designed to stop this process entirely. While these protections can be bypassed by expert security researchers, they can make a modernization project significantly more difficult and costly.
How long does this process take?
No. Success depends on the language the application was written in, the complexity of its logic, and whether the original developers used any anti-reverse engineering techniques. .NET and Java are generally the easiest to analyze; old C++ or Delphi applications are much harder.